I’m not sure why so much Indonesian virus maker using lot of this VBS technique (maybe they know without msvbvm.dll VBS can executed on a lot target), Since I write about VBS article long long time ago (I forget maybe around year 2003-2005) in jasakom website with title “VBS sederhana yang berbahaya” many people has try to manipulate that simple code to become advanced code. Now I’m fell really stupid by share that Article to public…
How to know if you’re infected by this worm VBS/Cryf.A:
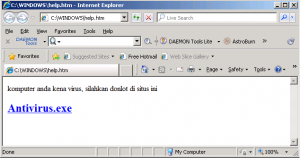
1.First time your computer turned on it will open web browser and show this pictures.
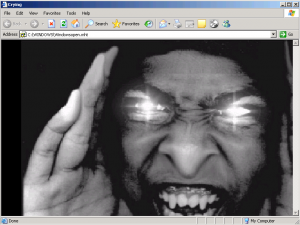
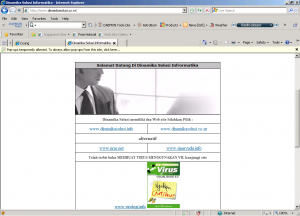
2. VBS/Cryf.A will change your web browser start page become:
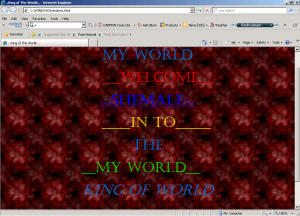
3. There is folder “album bokep” (in Indonesian language this mean porn) in all folder.
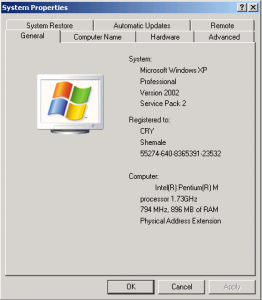
4. VBS/Cryf.A will change your system properties become like this:
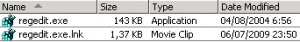
5. Change file type .lnk become “movie clip”
6. It will control your DVD/CD-rom by make it open and close to make you panic.
VBS/Cryf.A Master file:
VBS/Cryf.A has a master file called “drconfig.drv” with file size 218 KB, it already encrypted and little hard to read the code inside it.
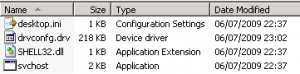
On first time active it will called “svchost.vbs” then this vbs will executed this “drconfig.drv”. Then it will started created file list:
* %Drive%\Recycled\S-1-5-21-343818398-18970151121-842a92511246-500\Thumbs.db
o svchost.vbs
o desktop.ini
o drvconfg.drv
o SHELL32.dll
* %Systemroot%\windows
o appsys.exe
o Winupdt.scx
o appopen.scx
o Windowsopen.mht
o Windows.html
o Regedit.exe.lnk
o Help.htm
* %Systemroot%\Windows\system\svchost.exe
* %Systemroot%\WINDOWS\system32
o Svchost.dls
o Corelsetup.scx
o Appsys.dls
o Kernel32.dls
o Taskmgr.exe.lnk
* %Systemroot%\WINDOWS\system32\
o Winupdtsys.exe
o ssmarque.scr
* %Systemroot%\Program Files\FarStone\qbtask.exe
* %Systemroot%\Program Files\ACDsee\Launcher.exe
* %Systemroot%\Program Files\Common Files\NeroChkup.exe
* %Systemroot%\Program Files\ExeLauncher
* %ProgramFiles%\drivers\VGA\VGAdrv.lnk
* %Systemroot%\Documents and Settings\%user%\Desktop\Local Disk (C).dls
This virus will make some action to keep him stay in computers target:
* Disable Task Manager
* Disable Regedit
* Disable CMD (Command Prompt)
* Disable MSConfig
* Can’t change wallpapers
It will change your screensaver like this:

Spreading Technique and Social Technique:
VBS/Cryf.A spreading using 2 technique, One of them as like in my first Article using autorun.inf files, beside that this virus maker know how to using social technique to tricky mostly people out there using porn movie that actually virus.
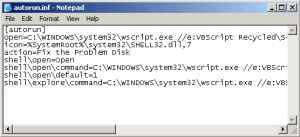
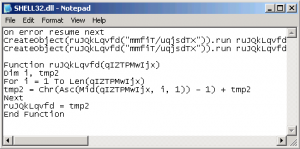
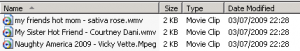
This virus maker try to manipulate people with his another social technique, he will try to tell people their computers infected and give the removal tools, actually don’t open that website (www.dinamikasolusi.co.nr) this virus maker maybe using some technique as I write a long time ago by insert some virus into computer target using html code.
Enough, let’s started to remove this stupid Worm VBS/Cryf.A
HOW TO REMOVE WORM VBS/Cryf.A:
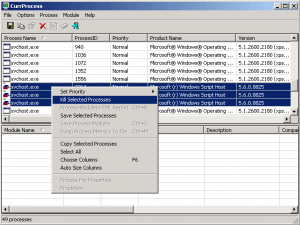
1. Kill active virus process in your background memory using currprocess, then kill all process with product name “Microsoft (r) Windows Script Host“
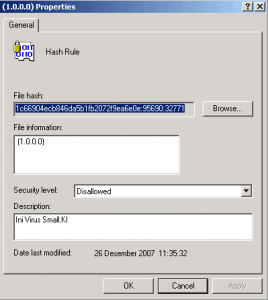
2. Block virus so it can not run for a while when we are in cleaning progress by:
Start -> Run -> Type “SECPOL.MSC” -> Click “software restriction policies” -> Click “additional rules” -> Right click on “additional rules” and choose “New Hash Rules”
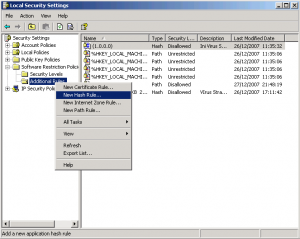
In “File Hash” Click on Browse and choose which file you want to block (WSScript.exe) on “Security level” choose Disalllowed then click OK.

3. Fix registry by using this 3rd tools, download it from HERE…
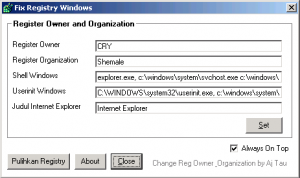


* Shell Windows = explorer.exe
* UserInit Windows
o Windows NT/2000 = C:\WinNT\System32\userinit.exe,
o Windows XP/2003/Vista = C:\Windows\System32\userinit.exe,
4. Deleted Virus Master files and all files he’s created. To help you deleted it in easy way I recommended to use this tools ExplorerXP, Then deleted all files list bellow:
* %Drive%\Recycled\S-1-5-21-343818398-18970151121-842a92511246-500\Thumbs.db
o svchost.vbs
o desktop.ini
o drvconfg.drv
o SHELL32.dll
* %Drive%\Album BOKEP\Naughty America
* %systemroot%\windows
o appsys.exe
o Winupdt.scx
o appopen.scx
o Windowsopen.mht
o Windows.html
o Regedit.exe.lnk
o Help.htm
* %systemroot%\Windows\system\svchost.exe
* %systemroot%\WINDOWS\system32
o Taskmgr.exe.lnk
o CMD.exe.lnk
o Svchost.dls
o Corelsetup.scx
o Appsys.dls
o Kernel32.dls
o Winupdtsys.exe
o ssmarque.scr
* %systemroot%\Program Files\FarStone\qbtask.exe
* %systemroot%\Program Files\ACDsee\Launcher.exe
* %systemroot%\Program Files\Common Files\NeroChkup.exe
* %systemroot%\Program Files\ExeLauncher
* %ProgramFiles%\drivers\VGA\VGAdrv.lnk
* %systemroot%\Documents and Settings\%user%\Desktop\Local Disk (C).dls
* %Flash Disk%\Dataku Penting Jangan Dihapus.lnk
5. Showing back your files TaskMgr.exe, Regedt32.exe, Regedit.exe, CMD.exe, and Logoff.exe that hidden by virus:
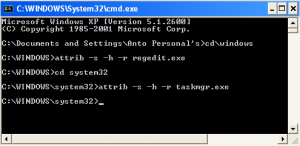
*repeated on all files you want to shown back.
6. For maximum cleaning I recommended to scan using your best antivirus programs, in my case Norman antivirus can deleted all of this virus part.
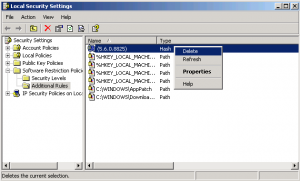
7. When all step done and no virus found, deleted blocking rules we made:
Start -> Run -> Type SECPOL.MSC -> Click “Software Restriction Policies” -> Click “Additional Rules” -> Then Deleted Rules we have made.
8. Restart your computer then re-scanned again to make sure there is no left part of worm VBS/Cryf.A, then use updated antivirus to prevent it coming back again.
Have a nice day, GBU :D

No comments:
Post a Comment